BitDepth 785 - June 07
06/06/11 23:27 Filed in: BitDepth - May 2011
A Trojan targets the Macintosh operating system.
Phishing for Mac users
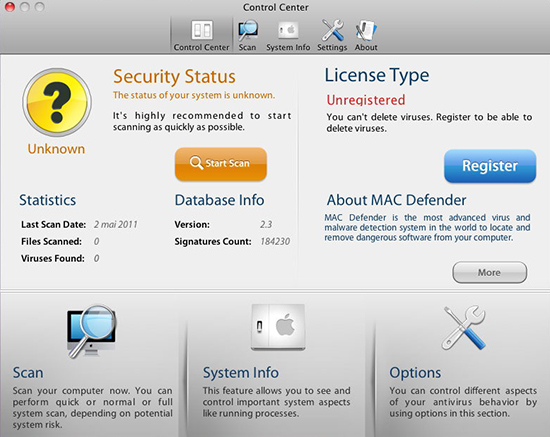
The impressively authentic control panel of the original MacDefender malware. Image courtesy Intego.
In early May, Macintosh users found themselves grappling with an unusual problem, a software Trojan Horse had infiltrated the normally virus-free halls of their operating system and was busy siphoning off cash from the unwary.
It was a story that I missed, despite seeing the web site for the fake anti-malware product more than a month ago. I have to confess to steupsing when I saw the slick but obvious attempt to prey on the gullibility of Mac owners with a product designed to search for largely nonexistent viruses.
After all, who would download this? Established anti-virus companies on the platform are struggling for business, often bundling their products for the Mac and PC to sell to Mac users who make use of the platform’s capacity to run both OS X and Microsoft’s Windows.
And just to be clear, a Mac running Windows, whether booted directly on the hardware or running in a virtualisation sandbox, is just as vulnerable to the threats directed at Windows as a regular PC is.
I run Windows Vista and Windows 7 in virtualisation on my desktop and portable respectively and the first thing I do when I start that software is to refresh my anti-virus definitions and add Microsoft’s newest updates.
I’m guessing that the folks who got conned by MacDefender are most likely to be recent Windows to Macintosh converts puzzled by the lack of warnings about potential threats and relatively low-keyed invitations to buy anti-virus and anti-malware software.
To them, MacDefender must have looked like a visitor from their old neighbourhood. Unfortunately, that’s exactly what it was.
The website hosting the software runs a fake scan of the user’s hard drive and invites them to download the “product.” If the user ignores the rather basic threat warnings built into Apple’s Safari browser about downloads, the product can then be launched, proceeding to find viruses while opening porn sites in the user’s web browser, reinforcing the “threat.”
After the scan, the software offers the spooked user an opportunity to buy the product for as much as US$100 for a “lifetime license” depending on the fear it's managed to invoke.
In the wake of increased awareness about the threat, a new variant, MacGuard (also known as MacSecurity and MacProtector) has surfaced which runs without requiring a user password, one of the key security measures built into Mac OS X.
After initially turning a cold shoulder to what was essentially a phishing scheme for inattentive users, Apple has since posted a note on its website advising users about the scheme with suggestions for victims.
The company has followed up on that with a security software update for its OS that's designed to guard against this specific threat. Within eight hours, the creators of the malware had created a variant of the scareware that sidesteps the new security measures.
The MacDefender incident should serve as a wake up call to both Macintosh customers and to Apple itself that while the platform has had few notable threats during its 20-year existence, its rising public profile and sales growth are likely to put it on the radar of the clever programmers keen to profit either through cash or reputation from seeding its devices with malicious code.
Apple must be prepared to more quickly and decisively than it has during the most confusing moments of the MacDefender threat.
Links
Apple’s knowledgebase note
Apple’s security update

The impressively authentic control panel of the original MacDefender malware. Image courtesy Intego.
In early May, Macintosh users found themselves grappling with an unusual problem, a software Trojan Horse had infiltrated the normally virus-free halls of their operating system and was busy siphoning off cash from the unwary.
It was a story that I missed, despite seeing the web site for the fake anti-malware product more than a month ago. I have to confess to steupsing when I saw the slick but obvious attempt to prey on the gullibility of Mac owners with a product designed to search for largely nonexistent viruses.
After all, who would download this? Established anti-virus companies on the platform are struggling for business, often bundling their products for the Mac and PC to sell to Mac users who make use of the platform’s capacity to run both OS X and Microsoft’s Windows.
And just to be clear, a Mac running Windows, whether booted directly on the hardware or running in a virtualisation sandbox, is just as vulnerable to the threats directed at Windows as a regular PC is.
I run Windows Vista and Windows 7 in virtualisation on my desktop and portable respectively and the first thing I do when I start that software is to refresh my anti-virus definitions and add Microsoft’s newest updates.
I’m guessing that the folks who got conned by MacDefender are most likely to be recent Windows to Macintosh converts puzzled by the lack of warnings about potential threats and relatively low-keyed invitations to buy anti-virus and anti-malware software.
To them, MacDefender must have looked like a visitor from their old neighbourhood. Unfortunately, that’s exactly what it was.
The website hosting the software runs a fake scan of the user’s hard drive and invites them to download the “product.” If the user ignores the rather basic threat warnings built into Apple’s Safari browser about downloads, the product can then be launched, proceeding to find viruses while opening porn sites in the user’s web browser, reinforcing the “threat.”
After the scan, the software offers the spooked user an opportunity to buy the product for as much as US$100 for a “lifetime license” depending on the fear it's managed to invoke.
In the wake of increased awareness about the threat, a new variant, MacGuard (also known as MacSecurity and MacProtector) has surfaced which runs without requiring a user password, one of the key security measures built into Mac OS X.
After initially turning a cold shoulder to what was essentially a phishing scheme for inattentive users, Apple has since posted a note on its website advising users about the scheme with suggestions for victims.
The company has followed up on that with a security software update for its OS that's designed to guard against this specific threat. Within eight hours, the creators of the malware had created a variant of the scareware that sidesteps the new security measures.
The MacDefender incident should serve as a wake up call to both Macintosh customers and to Apple itself that while the platform has had few notable threats during its 20-year existence, its rising public profile and sales growth are likely to put it on the radar of the clever programmers keen to profit either through cash or reputation from seeding its devices with malicious code.
Apple must be prepared to more quickly and decisively than it has during the most confusing moments of the MacDefender threat.
Links
Apple’s knowledgebase note
Apple’s security update
blog comments powered by Disqus

