BitDepth 765 - January 11
10/01/11 22:05 Filed in: BitDepth - January 2011
Production control systems are now being targeted by viruses written specifically to take them offline.
Cybercrime? Try cyberwarfare
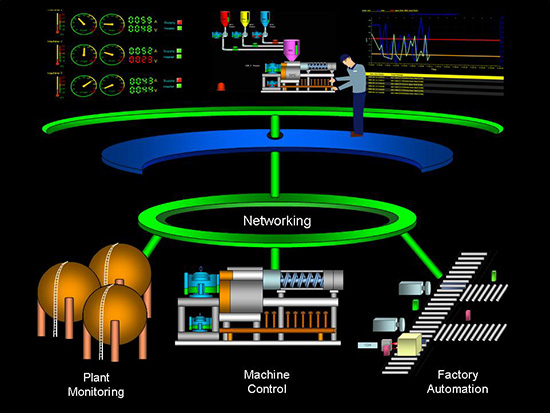
SCADA systems illustrated, from www.my-ias.com.
Early in October, Minister of National Security Brigadier John Sandy announced that the Government had begun working on plans for a National Cyber-security strategy.
“It was observed that the Internet has become a tool to commit and facilitate crime, which may result in devastating disruption in a nation’s critical infrastructure, economy and national security,” Minister Sandy announced.
The Security Minister seemed to have in mind the continuous attacks on networked computers and fraud schemes that proliferate on the Internet, but the stakes had been raised just weeks before with the discovery of the Stuxnet worm.
Unlike previous code written to infiltrate and damage computers, this software, since formally named SIMATIC WinCC and SIMATIC PCS 7, targeted industrial computer systems, specifically those running Supervisory Control And Data Acquisition systems commonly referred to as SCADA.
SCADA systems are widely used by the energy industry in Trinidad and Tobago to monitor and control remote rig and pump installations and is an integral part of the efficiencies that are part of the modern energy industry.
Stuxnet was written to reprogram the programmable logic controllers built into SCADA systems and appears to have been designed to specifically target controllers built by Siemens and used in nuclear power plants in Iran.
The efficiency and complexity of the Trojan and its wide spread in a specific target area have led to speculation that Stuxnet is the product of a nation with an interest in limiting Iran’s nuclear capabilities.
The software uses a number of sophisticated programming techniques to target Siemens’ Windows based control software and uses a number of zero day Windows exploits to extend its life in the field.
The code is so adaptable, resilient and well-armed with replication methods that it is not being considered an effort at mischief making. Stuxnet is one of the first widely disseminated computer programs that is aimed, with the deliberation and care of a sniper’s rifle, at the energy infrastructure of a nation state.
It was delivered to systems that aren’t normally networked with the outside world possibly on flash drives or diagnostic laptops.
It was, in short, not some disgruntled nerd’s angry response but an assault, programmed and specifically delivered with the precision and aggression of a military attack.
Stuxnet is encrypted, using keys that proved quite difficult to break, so the exact nature of the code remains unknown. What is known is that is becomes active in the presence of specific hardware, unlocks system passwords, utilises authentic digital signatures stolen from JMicron and Realtek and is capable of self-mutation and replication.
A total of 21 businesses running vulnerable Siemens systems reported infection by the Trojan. It’s likely that this effort was a proof of concept for the weaponising of virus code as a method of digital warfare.
The SCADA attack succeeded because nobody expected or planned for it. Despite warnings from the US General Accounting Office as early as 2004, machine control systems were seen as far removed from the run of day to day computer virus attacks and security strategies and prophylactic products were thin on the ground.
These are some of the new kinds of threats that the cross-border cybersecurity strategy being pursued by the National Security Minister will have to embrace and plan for, efforts at digital compromise that will come from directions currently undreamt and using techniques that leverage the weakest link in any digital security plan, people.
Links...
Siemens on the Trojan
Symantec’s 2006 report
Krebson Security’s 2007 warning
Andrew Ginter’s detailed explanation of the exploit

SCADA systems illustrated, from www.my-ias.com.
Early in October, Minister of National Security Brigadier John Sandy announced that the Government had begun working on plans for a National Cyber-security strategy.
“It was observed that the Internet has become a tool to commit and facilitate crime, which may result in devastating disruption in a nation’s critical infrastructure, economy and national security,” Minister Sandy announced.
The Security Minister seemed to have in mind the continuous attacks on networked computers and fraud schemes that proliferate on the Internet, but the stakes had been raised just weeks before with the discovery of the Stuxnet worm.
Unlike previous code written to infiltrate and damage computers, this software, since formally named SIMATIC WinCC and SIMATIC PCS 7, targeted industrial computer systems, specifically those running Supervisory Control And Data Acquisition systems commonly referred to as SCADA.
SCADA systems are widely used by the energy industry in Trinidad and Tobago to monitor and control remote rig and pump installations and is an integral part of the efficiencies that are part of the modern energy industry.
Stuxnet was written to reprogram the programmable logic controllers built into SCADA systems and appears to have been designed to specifically target controllers built by Siemens and used in nuclear power plants in Iran.
The efficiency and complexity of the Trojan and its wide spread in a specific target area have led to speculation that Stuxnet is the product of a nation with an interest in limiting Iran’s nuclear capabilities.
The software uses a number of sophisticated programming techniques to target Siemens’ Windows based control software and uses a number of zero day Windows exploits to extend its life in the field.
The code is so adaptable, resilient and well-armed with replication methods that it is not being considered an effort at mischief making. Stuxnet is one of the first widely disseminated computer programs that is aimed, with the deliberation and care of a sniper’s rifle, at the energy infrastructure of a nation state.
It was delivered to systems that aren’t normally networked with the outside world possibly on flash drives or diagnostic laptops.
It was, in short, not some disgruntled nerd’s angry response but an assault, programmed and specifically delivered with the precision and aggression of a military attack.
Stuxnet is encrypted, using keys that proved quite difficult to break, so the exact nature of the code remains unknown. What is known is that is becomes active in the presence of specific hardware, unlocks system passwords, utilises authentic digital signatures stolen from JMicron and Realtek and is capable of self-mutation and replication.
A total of 21 businesses running vulnerable Siemens systems reported infection by the Trojan. It’s likely that this effort was a proof of concept for the weaponising of virus code as a method of digital warfare.
The SCADA attack succeeded because nobody expected or planned for it. Despite warnings from the US General Accounting Office as early as 2004, machine control systems were seen as far removed from the run of day to day computer virus attacks and security strategies and prophylactic products were thin on the ground.
These are some of the new kinds of threats that the cross-border cybersecurity strategy being pursued by the National Security Minister will have to embrace and plan for, efforts at digital compromise that will come from directions currently undreamt and using techniques that leverage the weakest link in any digital security plan, people.
Links...
Siemens on the Trojan
Symantec’s 2006 report
Krebson Security’s 2007 warning
Andrew Ginter’s detailed explanation of the exploit
blog comments powered by Disqus

